生辰八字五行宝宝起名软件V23.6算法分析
即使看见高峰论坛没人须要那个应用软件的演算法预测,因此无趣就写出这首诗和他们一同研习,这篇演算法预测较为适宜初学者自学,即使演算法非常简单。 该应用软件是两个杨林应用软件,因此间接下杨林按键该事件葡乙,找关键性的演算法call004A802A /. 55 push ebp ; 注册登记演算法004A802B |. 8BEC mov ebp,esp004A802D |. 81EC 34000000 sub esp,0x34004A8033 |. C745 FC 00000>mov[local.1],0x0004A803A |. C745 F8 00000>mov[local.2],0x0004A8041 |. C745 F4 00000>mov[local.3],0x0004A8048 |. 6A 01 push 0x1004A804A |. B8 ED6F6D00 mov eax,属相.006D6FED ; wenyuhao004A804F |. 8945 F0 mov [local.4],eax004A8052 |. 8D45 F0 lea eax,[local.4]004A8055 |. 50 push eax004A8056 |. 68 D0C38A00 push 属相.008AC3D0 ; 8}Z\t004A805B |. 68 84C48A00 push 属相.008AC484下面这段是演算法的已经开始,他们一步棋一步棋预测,即使那个演算法非常简单,适宜初学者去自学展枝!!004A812C |. 83C4 04 add esp,0x4004A812F |> 58 pop eax004A8130 |. 8945 FC mov [local.1],eax004A8133 |. 6A FF push -0x1004A8135 |. 6A 08 push 0x8004A8137 |. 68 0F940216 push 0x1602940F004A813C |. 68 27540152 push 0x52015427004A8141 |. E8 82E40800 call 属相.005365C8 ; 以获取我输出的假码004A8146 |. 83C4 10 add esp,0x10004A8149 |. 8945 F0 mov [local.4],eax004A814C |. 68 04000080 push 0x80000004004A8151 |. 6A 00 push 0x0004A8153 |. 8B45 F0 mov eax,[local.4]004A8156 |. 85C0 test eax,eax004A8158 |. 75 05 jnz short 属相.004A815F
该应用软件是两个杨林应用软件,因此间接下杨林按键该事件葡乙,找关键性的演算法call004A802A /. 55 push ebp ; 注册登记演算法004A802B |. 8BEC mov ebp,esp004A802D |. 81EC 34000000 sub esp,0x34004A8033 |. C745 FC 00000>mov[local.1],0x0004A803A |. C745 F8 00000>mov[local.2],0x0004A8041 |. C745 F4 00000>mov[local.3],0x0004A8048 |. 6A 01 push 0x1004A804A |. B8 ED6F6D00 mov eax,属相.006D6FED ; wenyuhao004A804F |. 8945 F0 mov [local.4],eax004A8052 |. 8D45 F0 lea eax,[local.4]004A8055 |. 50 push eax004A8056 |. 68 D0C38A00 push 属相.008AC3D0 ; 8}Z\t004A805B |. 68 84C48A00 push 属相.008AC484下面这段是演算法的已经开始,他们一步棋一步棋预测,即使那个演算法非常简单,适宜初学者去自学展枝!!004A812C |. 83C4 04 add esp,0x4004A812F |> 58 pop eax004A8130 |. 8945 FC mov [local.1],eax004A8133 |. 6A FF push -0x1004A8135 |. 6A 08 push 0x8004A8137 |. 68 0F940216 push 0x1602940F004A813C |. 68 27540152 push 0x52015427004A8141 |. E8 82E40800 call 属相.005365C8 ; 以获取我输出的假码004A8146 |. 83C4 10 add esp,0x10004A8149 |. 8945 F0 mov [local.4],eax004A814C |. 68 04000080 push 0x80000004004A8151 |. 6A 00 push 0x0004A8153 |. 8B45 F0 mov eax,[local.4]004A8156 |. 85C0 test eax,eax004A8158 |. 75 05 jnz short 属相.004A815F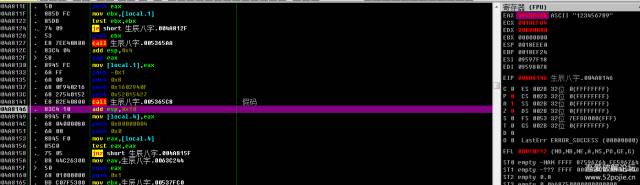
004A8182 |. 83C4 04 add esp,0x4004A8185 |> 68 45C26300 push 属相.0063C245 ;004A818A |. FF75 EC push [local.5]004A818D |. 68 3BDB6E00 push 属相.006EDB3B ; pass=004A8192 |. B9 03000000 mov ecx,0x3004A8197 |. E8 B292F5FF call 属相.0040144E004A819C |. 83C4 0C add esp,0xC004A819F |. 8945 E8 mov [local.6],eax004A81A2 |. 8B5D EC mov ebx,[local.5]004A81A5 |. 85DB test ebx,ebxPass=和假码合并pass=123456789然后一直下去会进行一些没关紧要的操作,这些可以忽略不理。004A8234 |. 83C4 04 add esp,0x4004A8237 |> 58 pop eax004A8238 |. 8945 F8 mov [local.2],eax004A823B |. 6A FF push -0x1004A823D |. 6A 08 push 0x8004A823F |. 68 0F940216 push 0x1602940F004A8244 |. 68 27540152 push 0x52015427004A8249 |. E8 7AE30800 call 属相.005365C8 继续取出假码004A824E |. 83C4 10 add esp,0x10004A8251 |. 8945 F0 mov [local.4],eax004A8254 |. 68 04000080 push 0x80000004004A8259 |. 6A 00 push 0x0004A825B |. 8B45 F0 mov eax,[local.4]004A825E |. 85C0 test eax,eax004A8260 |. 75 05 jnz short 属相.004A8267
----------------------------------------------
004A828A |. 83C4 04 add esp,0x4004A828D |> 68 45C26300 push 属相.0063C245 ;004A8292 |. FF75 EC push [local.5]004A8295 |. 68 3BDB6E00 push 属相.006EDB3B ; pass=004A829A |. B9 03000000 mov ecx,0x3004A829F |. E8 AA91F5FF call 属相.0040144E004A82A4 |. 83C4 0C add esp,0xC004A82A7 |. 8945 E8 mov [local.6],eax004A82AA |. 8B5D EC mov ebx,[local.5]004A82AD |. 85DB test ebx,ebx继续Pass=和假码合并pass=123456789
----------------------------------------------
004A833C |. 83C4 04 add esp,0x4004A833F |> 58 pop eax004A8340 |. 8945 F4 mov [local.3],eax004A8343 |. 68 04000080 push 0x80000004004A8348 |. 6A 00 push 0x0004A834A |. A1 D4C38A00 mov eax,dword ptr ds:[0x8AC3D4] ; 机器码序列号,请记下那个全局变量[0x8AC3D4]004A834F |. 85C0 test eax,eax我这里的机器码为:2018682084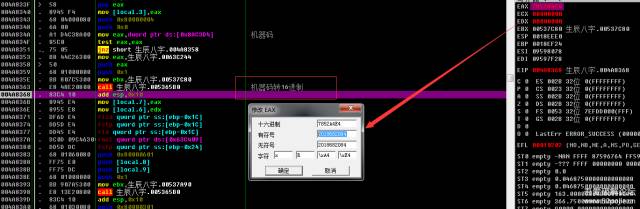
004A8368 |. 83C4 10 add esp,0x10004A836B |. 8945 E4 mov [local.7],eax004A836E |. 8955 E8 mov [local.6],edx004A8371 |. DF6D E4 fild qword ptr ss:[ebp-0x1C]004A8374 |. DD5D E4 fstp qword ptr ss:[ebp-0x1C]004A8377 |. DD45 E4 fld qword ptr ss:[ebp-0x1C]004A837A |. DC0D 09C46300 fmul qword ptrds:[0x63C409] ; 机器码×323 注意这里的操作都是以10进制操作004A8380 |. DD5D DC fstp qword ptr ss:[ebp-0x24]004A8383 |. 68 01060080 push 0x80000601004A8388 |. FF75 E0 push [local.8]004A838B |. FF75 DC push [local.9]004A838E |. 6801000000 push 0x1004A8393 |. BB 907A5300 mov ebx,属相.00537A90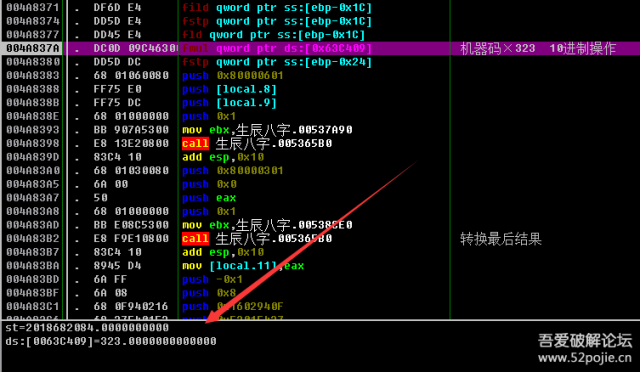
这里是机器码*3232018682084*323= hex (D0460BAC)
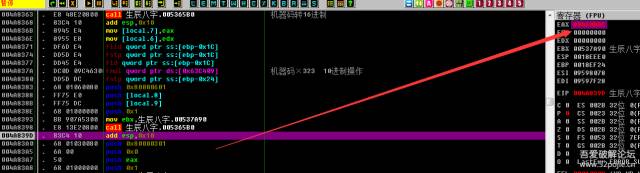
004A839D |. 83C4 10 add esp,0x10004A83A0 |. 68 01030080 push 0x80000301004A83A5 |. 6A 00 push 0x0004A83A7 |. 50 push eax004A83A8 |. 68 01000000 push 0x1004A83AD |. BB E08C5300 mov ebx,属相.00538CE0004A83B2 |. E8 F9E10800 call 属相.005365B0 ; 将结果转换为10进制004A83B7 |. 83C4 10 add esp,0x10004A83BA |. 8945 D4 mov [local.11],eax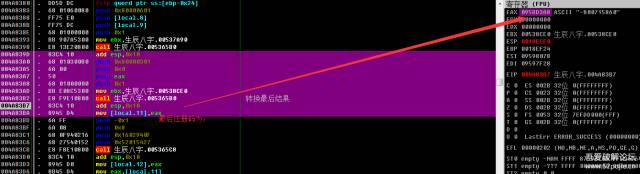
经典的杨林文本较为004A83D0 |. 83C4 10 add esp,0x10004A83D3 |. 8945 D0 mov [local.12],eax004A83D6 |. 8B45 D4 mov eax,[local.11]004A83D9 |. 50 push eax004A83DA |. FF75 D0 push [local.12]004A83DD |. E8 648FF5FF call 属相.00401346004A83E2 |. 83C4 08 add esp,0x8004A83E5 |. 83F8 00 cmp eax,0x0004A83E8 |. B8 00000000 mov eax,0x0004A83ED |. 0F94C0 sete al004A83F0 |. 8945 CC mov [local.13],eax004A83F3 |. 8B5D D0 mov ebx,[local.12]004A83F6 |. 85DB test ebx,ebx
爆破的话修改下面跳转就可以了,他们现在是学演算法预测,因此他们不玩爆破。总结:注册登记码=机器码* 323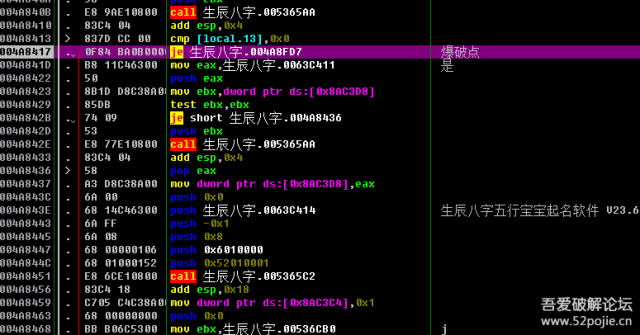
知道了注册登记码怎么计算出来的,现在他们来找出机器码的演算法。刚才叫他们记下那个全局变量[0x8AC3D4]现在他们搜索那个常量
全部都下上断点00401F16 . 5E pop esi ; 057ACA3000401F17 . 8BF8 mov edi,eax00401F19 . F3:A4 rep movs byte ptr es:[edi],byte ptrds:[>00401F1B > 50 push eax00401F1C . 8B1D D4C38A00 mov ebx,dword ptrds:[0x8AC3D4]00401F22 . 85DB test ebx,ebx00401F24 . 74 09 je short 属相.00401F2F00401F26 . 53 push ebx00401F27 . E8 7E461300 call 属相.005365AA00401F2C . 83C4 04 add esp,0x4他们发现在这里葡乙,这时候,eax已经出现了机器码,他们往上找,看看机器码怎么计算出来的。00401DDD . 6A 00 push 0x000401DDF . 6A 00 push 0x000401DE1 . 6A 00 push 0x000401DE3 . 68 07000700 push 0x7000700401DE8 . 6A 00 push 0x000401DEA . FF35 CCC38A00 push dword ptrds:[0x8AC3CC]00401DF0 . 68 02000000 push 0x200401DF5 . B8 06000000 mov eax,0x600401DFA . BB 60965C00 mov ebx,属相.005C966000401DFF . E8 B8471300 call 属相.005365BC00401E04 . 83C4 1C add esp,0x1C00401E07 . 8B1D CCC38A00 mov ebx,dword ptr ds:[0x8AC3CC]00401E0D . 83C3 08 add ebx,0x800401E10 . 895D FC mov dword ptr ss:[ebp-0x4],ebx00401E13 . 68 04000080 push 0x8000000400401E18 . 6A 00 push 0x000401E1A . 8B5D FC mov ebx,dword ptr ss:[ebp-0x4]00401E1D . 8B03 mov eax,dword ptr ds:[ebx]00401E1F . 85C0 test eax,eax00401E21 . 75 05 jnz short 属相.00401E2800401E23 . B8 44C26300 mov eax,属相.0063C24400401E28 > 50 push eax00401E29 . 68 01000000 push 0x100401E2E . BB 10845300 mov ebx,属相.00538410这里是取硬盘序列号我这里是 S248NXAH110569Z00401E51 > \50 push eax00401E52 . 68 01000000 push 0x100401E57 . B8 0E000000 mov eax,0xE00401E5C . BB 20E65D00 mov ebx,属相.005DE62000401E61 . E8 56471300 call 属相.005365BC00401E66 . 83C4 10 add esp,0x1000401E69 . 8945 F4 mov dword ptr ss:[ebp-0xC],eax00401E6C . 8B5D F8 mov ebx,dword ptr ss:[ebp-0x8]00401E6F . 85DB test ebx,ebx ; 属相.005DE620将硬盘序列号进行MD5操作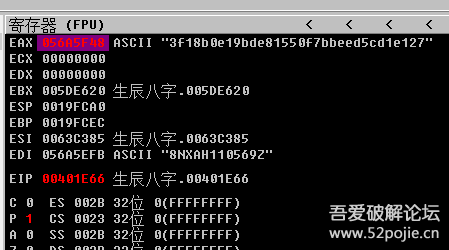 00401E93 > \58 pop eax00401E94 . A3 D0C38A00 mov dword ptr ds:[0x8AC3D0],eax00401E99 . 68 00000000 push 0x000401E9E . BB F0CC5300 mov ebx,属相.0053CCF000401EA3 . E8 08471300 call 属相.005365B000401EA8 . 83C4 04 add esp,0x400401EAB . 8945 F4 mov dword ptr ss:[ebp-0xC],eax00401EAE . DB45 F4 fild dword ptr ss:[ebp-0xC]00401EB1 . DD5D F4 fstp qword ptr ss:[ebp-0xC]00401EB4 . DD45 F4 fld qword ptr ss:[ebp-0xC]00401EB7 . DC05 F2C36300 fadd qword ptrds:[0x63C3F2]00401EBD . DD5D EC fstp qword ptr ss:[ebp-0x14]00401EC0 . 68 01060080 push 0x8000060100401EC5 . FF75 F0 push dword ptr ss:[ebp-0x10]00401EC8 . FF75 EC push dword ptr ss:[ebp-0x14] ; 属相.008B868000401ECB . 68 01000000 push 0x100401ED0 . BB E08C5300 mov ebx,属相.00538CE0这段其实是杨林的取硬盘特征字命令,我在这里浪费了不少时间才得知是那个命令00401EA3 . E8 08471300 call 属相.005365B0 F7进入
00401E93 > \58 pop eax00401E94 . A3 D0C38A00 mov dword ptr ds:[0x8AC3D0],eax00401E99 . 68 00000000 push 0x000401E9E . BB F0CC5300 mov ebx,属相.0053CCF000401EA3 . E8 08471300 call 属相.005365B000401EA8 . 83C4 04 add esp,0x400401EAB . 8945 F4 mov dword ptr ss:[ebp-0xC],eax00401EAE . DB45 F4 fild dword ptr ss:[ebp-0xC]00401EB1 . DD5D F4 fstp qword ptr ss:[ebp-0xC]00401EB4 . DD45 F4 fld qword ptr ss:[ebp-0xC]00401EB7 . DC05 F2C36300 fadd qword ptrds:[0x63C3F2]00401EBD . DD5D EC fstp qword ptr ss:[ebp-0x14]00401EC0 . 68 01060080 push 0x8000060100401EC5 . FF75 F0 push dword ptr ss:[ebp-0x10]00401EC8 . FF75 EC push dword ptr ss:[ebp-0x14] ; 属相.008B868000401ECB . 68 01000000 push 0x100401ED0 . BB E08C5300 mov ebx,属相.00538CE0这段其实是杨林的取硬盘特征字命令,我在这里浪费了不少时间才得知是那个命令00401EA3 . E8 08471300 call 属相.005365B0 F7进入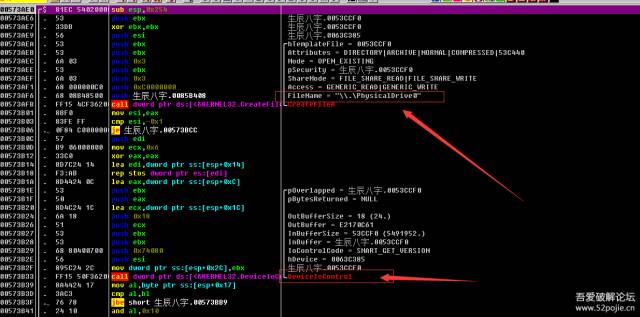
百度了一下上图圈出的关键性字,得出是取硬盘信息相关的命令。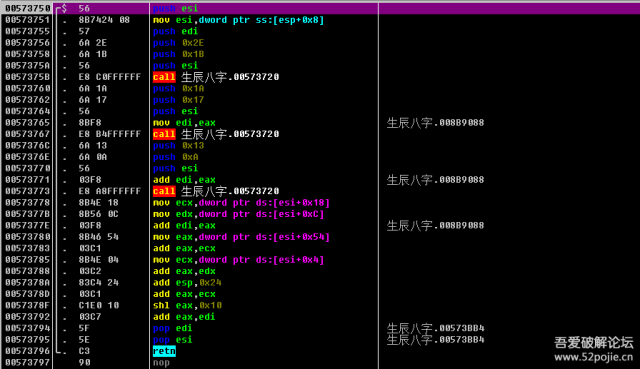
上图这段是进行各种硬盘信息操作,得出最后的取硬盘特征字 把硬盘模型号的ASCII进行相加
把硬盘模型号的ASCII进行相加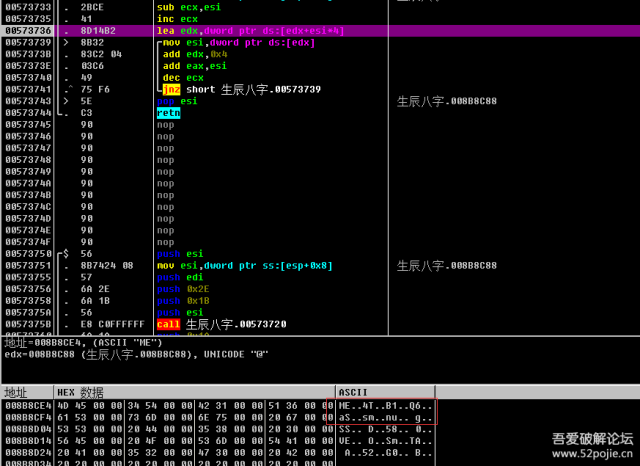 拿出硬盘版本 EMT41B6Q 进行ASCII相加其他几个就不一一说了,都是拿下面这些信息进行运算。硬盘模型号 Samsung SSD 850 EVO mSATA250GB版本 EMT41B6Q硬盘序列号 S248NXAH110569Z磁头数 16柱面数 266305容量 131071缓存大小 0每磁道扇区数 63第一硬盘特征字是:1079414944
拿出硬盘版本 EMT41B6Q 进行ASCII相加其他几个就不一一说了,都是拿下面这些信息进行运算。硬盘模型号 Samsung SSD 850 EVO mSATA250GB版本 EMT41B6Q硬盘序列号 S248NXAH110569Z磁头数 16柱面数 266305容量 131071缓存大小 0每磁道扇区数 63第一硬盘特征字是:1079414944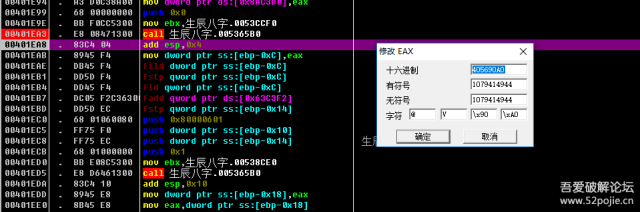 最后得出第一硬盘特征字是:1079414944
最后得出第一硬盘特征字是:1079414944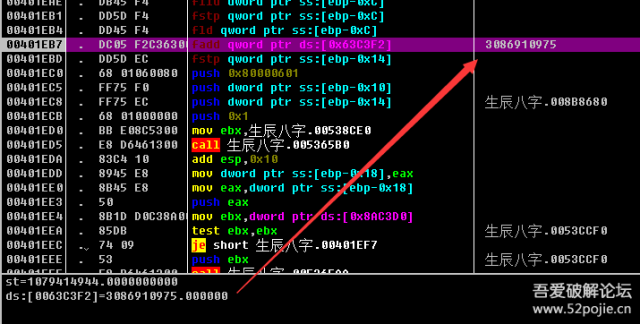 然后将盘特征字和3086910975进行相加操作,最后就得出机器码。
然后将盘特征字和3086910975进行相加操作,最后就得出机器码。 附上应用软件和KeyGen链接:https://share.weiyun.com/89dd392ddbbb753f64c10dcb21a7e758(密码:NYXK9I)
附上应用软件和KeyGen链接:https://share.weiyun.com/89dd392ddbbb753f64c10dcb21a7e758(密码:NYXK9I)
--官方高峰论坛
www.52pojie.cn
--推荐给朋友
公众微信号:吾爱破解高峰论坛
或搜微信号:pojie_52

相关文章
发表评论
评论列表
- 这篇文章还没有收到评论,赶紧来抢沙发吧~

![给苹果手机取名字大全有趣幽默的[有趣的苹果手机的名字]](http://xingzuo.gpyd.cn/zb_users/theme/themeolBkTwo/include/random/2.jpg)
![农业公司取名字参考大全2-3个字[取个农业公司名称大全]](http://xingzuo.gpyd.cn/zb_users/theme/themeolBkTwo/include/random/4.jpg)